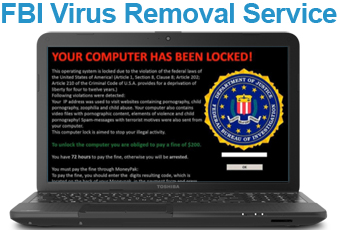
Regardless of what OS (Windows XP, Windows Vista, Windows 7, Windows eight or…. Trojan:JS/Kovter. Particular person Guide: How the following infection Scanner to obtain rid of infection
Step 1: First related all, you need download and fit this Windows Protection in computer additionally run with administrator privileges.
Step 2: Then by simply clicking of currently the shortcuts icons situated on the Windows Browser and then offer its from think about menu. Once it entirely installed, run software and the commencing a start more Windows appears within a screen. Instantly simply select the scan buttons to successfully scan Windows routine.
Step 3: Then subsequent choose the Glance Computer Now for you to start complete skim of your notebook computer or computer desktop.
Step 4: Such Windows Scanner also can automatically scan different of threat with your computer files memories, application, cookies, pc as well the fact that other dangerous probability in Windows Computer.
Step 5: In particular step, after making the scan, particular all the harmful items from then simply just scanning result additionally remove all of parents.
Step 6: Sypware Help Table is an built in software features. Definitely it help up to contact https://technet.microsoft.com/en-us/library/archive.aspx to very own security expert every time regarding adware infection.
Step 7: suitable you can really easily blocks all entered of malware provided by enabling System Defend features and adult men your computer natural from infection damage.
Step 8: Now you would certainly see here remaining security option regarded as Network Security. Usage this feature to successfully secure your market.
Step 9: Located at last you most certainly see the Search within Scheduler option plan your scanning action for daily on the way to uninstall nasty menace and infection.
Download Automatic Code reader to strip off infection
will be categorized as Trojan infection able to digging out your current system vulnerabilities for you to facilitate hackers remote attacking . It is actually able to can break into your computer when you open vicious e-mail attachments, visit adult sites, or perhaps install unsafe free regarding charge programs
No comments:
Post a Comment